As part of an event sponsored by the Internet of Things Community, Intertrust’s Julian Durand, Vice President, Product Management and CISO, gave a talk entitled “The IoT is Breeding Killer Botnets. Device Authentication and Data Integrity can save IT.” While the title is a bit of a mouthful, the gist of Durand’s presentation is that botnets and other attacks are on the rise and are a very real threat to IoT devices and the services that depend on them. The good news is that an IoT standard developed by the U.S. Government’s National Institute of Standards and Technology (NIST) is playing an important role in helping to keep IoT devices and services safe. Implementing device authentication and data integrity are critical to IoT security and meeting the NIST standard.
Durand highlighted a number of threats and hacks to IoT devices, but the one he focused on is what are called botnets. Botnets are networks of devices that have been hacked by a bad actor and can be used for cyber attacks such as denial of service attacks. “Botnets used to consist mainly of desktop PCs, but now it is more common to use video cameras, set top boxes, anything with insufficient security that can be taken over,” said Durand. Botnets are on the rise. Durand quoted from a Fortinet report that showed that botnets detected within organizations had risen from 35.1% in January 2021 to 51.4% in June 2021.
While there are a number of types of botnet malware active in the field, Durand focused on the Mirai malware. Noted Durand, “Mirai is not sophisticated but it has been long lasting.” Essentially a Mirai attacker uses a server to scan for devices with known vulnerabilities. The attacker then exploits those vulnerabilities to place the Mirai malware on these devices and control them from a command and control server. Vulnerabilities that bad actors can exploit range from software with known vulnerabilities that hasn’t been updated to devices using the default security credentials they were shipped with. According to Durand, these default credentials are well known amongst bad actors and sold cheaply on the Dark Web.
The increasing number of botnets and other hacks has risen to the point where these are now major threats to our economy. This is aptly demonstrated by the “Black Energy” attack on the Ukrainian electrical grid in 2015 and “NotPetya” attacks of 2017. The good news is that many of these attacks can be avoided just by using well-established security practices. These include ensuring that each device is properly identified using secure identification techniques and the software on the device can only be updated by authorized entities.
NIST to the rescue
The U.S. Government recognized the need to establish policy responses to these threats. A Presidential executive order was published in May 2017, followed by the passage of the Internet of Things Cybersecurity Improvement Act of 2020 by the U.S. Congress. One of the the results of this activity is NIST publishing and the further promotion of “NISTIR 8259A IoT Device Cybersecurity Capability Core Baseline”. As illustrated in the graphic below, the NIST Baseline calls for the implementation of a number of security measures to protect IoT devices. The U.S. government is required to only buy devices that comply with the NIST Baseline. Given the size of the U.S. Government, previous NIST security frameworks have led to broad adoption in the industry. Accordingly, “the NIST Baseline is a potential game changer,” said Durand.
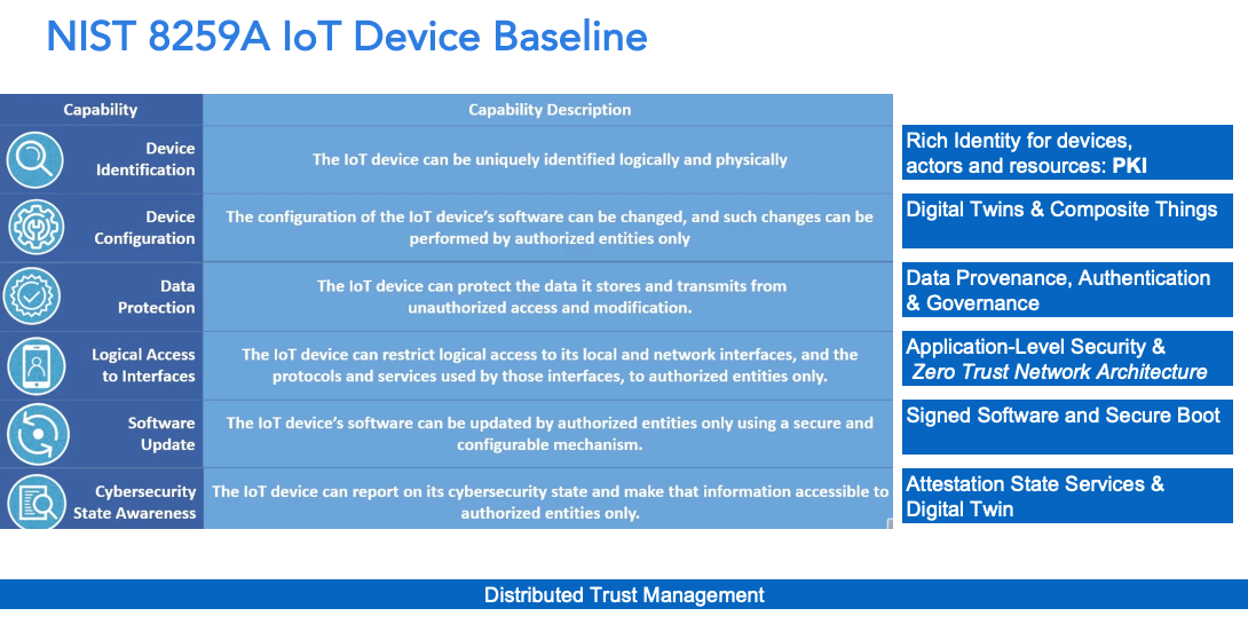
There are two key technical measures called out by the NIST Baseline. One is the need for secure device authentication. Durand pointed out that devices can be “spoofed” and that “device identification is needed for device authentication.” PKI-based certificates, such as the ones offered by Intertrust PKI, are the industry standard and market proven method of device authentication. They are also one of the bedrock security technologies that other measures such as secure boot and secure software updates are built upon. Durand also notes that “we should think beyond the simplest scenarios,” and explore expanded or rich identities that can authenticate any number of the capabilities of a device, further increasing its security.
The other one is secure data integrity. Since a wide variety of critical actions could be taken based on data coming from IoT devices, the data stored by the device as well as the data transmitted by the device needs to be secured and trusted. Again, device authentication is a baseline necessity for data authentication measures such as data encryption. Device authentication is also needed for adding additional capabilities to maintain data integrity as it potentially travels over untrusted networks and devices on its path to its final consumer.
IoT device manufacturers and their customers and ecosystem partners are well advised to add NIST Baseline compliance to their product roadmaps. Intertrust PKI and Intertrust Platform are useful building blocks for these efforts.